

Sharkfest 2016 recap
Another Sharkfest has come and gone, and once again it has been a great conference. If you’re into packet analysis, network forensics or network troubleshooting there is no other event that has the same density of information. It’s really a “specialist” conference, in a very open and friendly way, and newcomers are always welcome.

Megalodon challenge solution
During Sharkfest 2015 I put up a challenge that was different from the usual challenges offered. The pcap files are a lot bigger, the task to solve less specific, and the answer not a simple “easy to verify” answer. I promised to put up my solution a few months after posting the challenge to this blog, but then some things got in the way. And then… some more got in the way. Sorry for that, but sometimes it can’t be helped.
Verifying IoCs with Snort and TraceWrangler
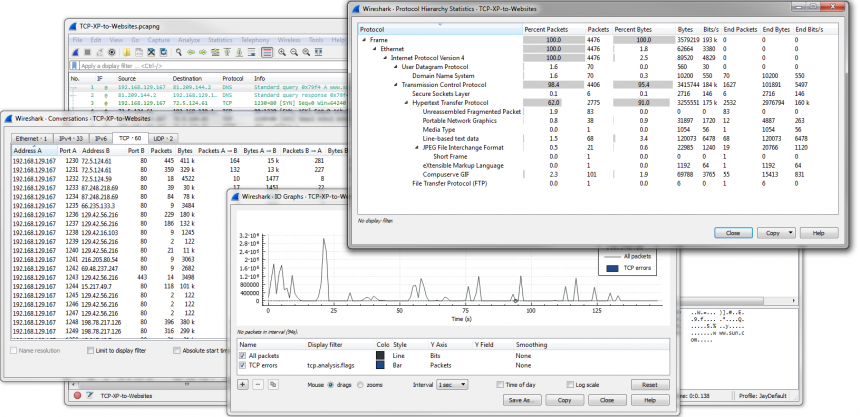
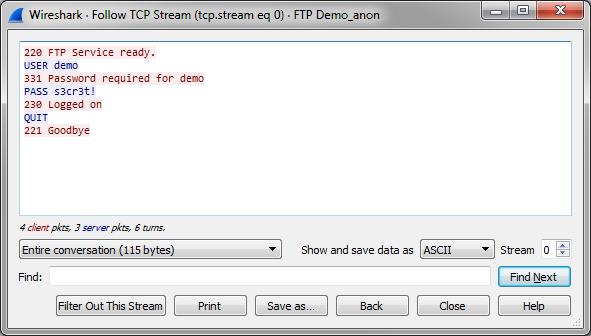
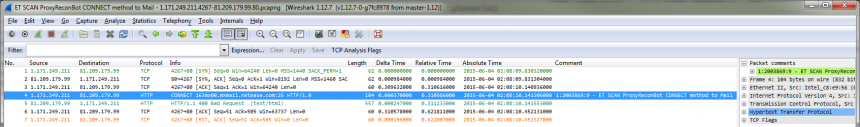
After detecting a network breach it is a good idea to scan the network for further Indicators of Compromise (IoC) to check for further malicious activity. The IoCs are usually derived from forensic investigations into network packets and compromised hosts, and can be quite unique when it comes to more sophisticated attacks (let’s avoid mentioning the APT buzzword here… oh, wait… darn!).
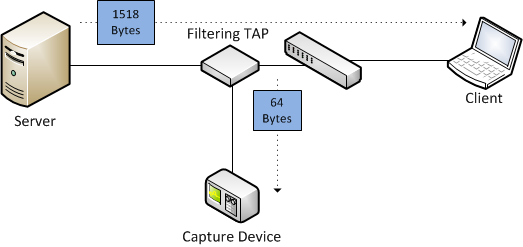
Frame bytes vs. frame file headers
When capturing frames from a network there is more information recorded into the capture file than just the bytes of each frame. If you have ever looked at the PCAP or PCAPng file format specifications you have seen that each frame has an additional frame header containing important information that wasn’t part of the frame itself.

The Megalodon Challenge
This year at Sharkfest I offered a special capture file challenge I called “The Megalodon Challenge”. Other than the “normal” challenges you could find at The Reef it was not limited to the size of 100MB, and the solution cannot be reduced to a couple of words or numbers. After Sharkfest I was asked if I could put up the challenge so that people that haven’t been at the conference (or didn’t know about the challenge) could give it a shot. So here it is.

Sharkfest 2015 recap
“Jasper, do you have a minute?”
I think that is the one sentence that I heard most at Sharkfest 2015, which is the annual Wireshark developer and user conference. Which makes it the most interesting place to be for anyone doing network analysis, for business or fun/hobby (yes, those exist). People asking me for a minute involved Wireshark core developers, other speakers, and of course Sharkfest attendees.
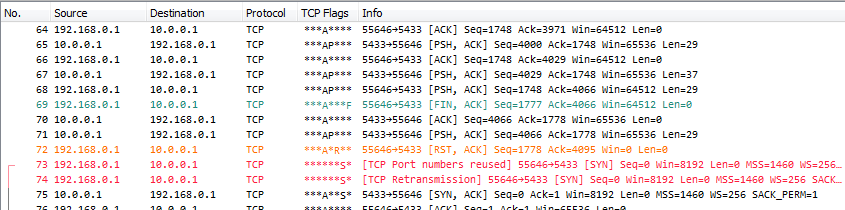
Port Numbers reused
Sharkfest 2015 is coming up fast (22 days, 12 hours to go when typing this), and so I spend the morning hours of my Saturday for preparation of materials for my three talks. Since that also involves adding features and fixing bugs in TraceWrangler (which I also need for the large demo part of my FIRST presentation the week before Sharkfest) it is a slow process. So let’s waste a little additional time on a blog post 🙂
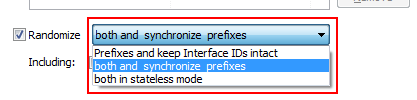
Sanitizing IPv6 addresses
Tracewrangler was always supporting IPv6 from the start (even though without extension headers except fragmentation), but last weekend I realized that I could improve the sanitization feature due to something that is missing compared to IPv4: subnet masks. This may sound funny, but in fact the missing subnet masks help.

Recent Comments