A creative way of refusing connections
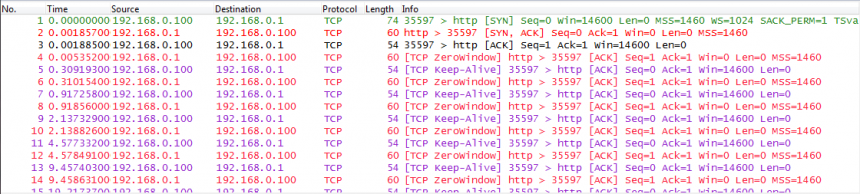
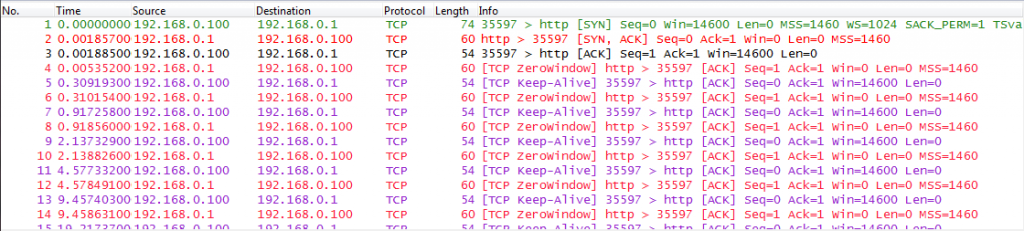
A few days ago, Olli, one of our team members, sent me a funny trace that he’d taken while configuring the security settings on a Netoptics Bypass kit. This device has an SNMP and HTTP management service, and when he disabled the HTTP service he verified if the setting was accepted (like you should). Usually, there would either be a Reset packet coming back when a SYN is sent, or no answer at all. To his surprise, the device behaved a little different than expected.
Instead of rejecting the connection it accepts the Three Way Handshake, but keeps sending a Window size of zero back to the client, effectively stalling the connection. I have no idea why the NetOptics engineers implemented it this way, when a Reset or no answer at all would be enough to say “You shall not pass!”. Our guess is that maybe they wanted to slow down attackers this way by doing tarpitting for TCP scans…

Discussions — No responses yet