The trouble with multiple capture interfaces
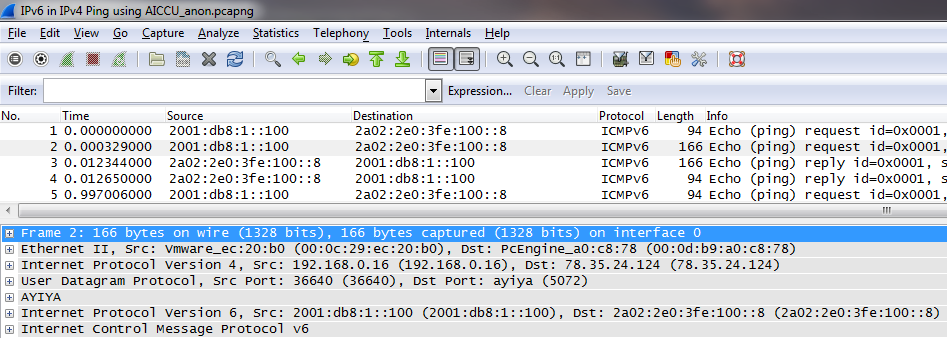
The PCAPng file format
Starting with Wireshark 1.8, the old PCAP format was replaced by PCAPng as the new default file format for packet captures. I have to admit that I may be one of the people to blame for this – at the end of Sharkfest 2011 we had a panel discussion with Gerald and some other guys when the topic of PCAPng support came up.


Recent Comments