Cisco Live – Network Building Blocks for IoT
Cisco Live happened in Barcelona end of January, and as usual I am a little late with my blog posts about it. Like the last two years I was invited to join the group of technology experts for Tech Field Day Extra, with various presentations covering a number of new and improved Cisco technologies as well as some Cisco partner products.
I’m always a little outside my comfort zone when it comes to the higher level product line that Cisco offers, even though I understand what those are good for. Cisco has realized that we need to move past the paradigm of “configure each device separately on the CLI” and instead automate all the “trivial” stuff as much as possible. That’s why there are concepts like Cisco ACI and tools like Cisco DNA – but since I don’t work with them at all I don’t have any hands-on knowledge. Which is why I focus on other topics – and one that I always liked was when it gets low level. Electrical level, that is. Which means ASICs, switches, and all the other building blocks.
Switching and Routing in harsh environments
With all the fancy tools that now seem to take over network operations it is easy to forget that those tools need a solid foundation. If you build a tall building on sand you’re not going to be happy, and the same applies to networks. The building blocks that provide the actual connectivity need to be fast, they need to be reliable, and – last but not least – they need to be improved and adopted to new challenges coming up. Challenges like harsh environments, e.g. very cold or very hot locations where IT devices weren’t used so far. And that means IoT.
Yes, I know, IoT is a huge buzzword, and usually I roll my eyes when people mention it (mostly because the S in IoT stands for “Security”). Right. Not secure. By the way, the other thing that really annoys me about IoT is that many of those devices come with a custom network stack – and those are often buggy as hell. I can’t count how many times I saw a pcap file where the communication failed because someone didn’t realize how CRCs are calculated, or even how auto negotiation or MAC addressing works. We used to be past that stage for a decade or two… *sigh*
Anyway, one of the presentations at Cisco Live was by Tim Szigeti, about IoT switches and routers Cisco added to their portfolio:
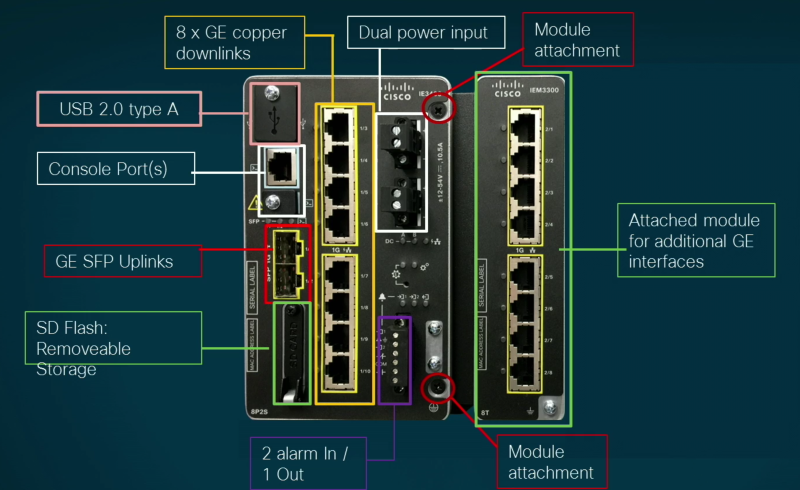
The advantage of having rugged Cisco equipment to provide connectivity IoT edge computing is that it’s not just the connectivity it offers, but the additional functionality that comes with having the well know IOS operating system running on them. The have the same features and capabilities like the “normal” routers and switches, and they can be managed using Cisco DNA center. The switch can also be expanded with add-on modules to add more interfaces if required (more than one, if you want):
The rugged switch will boot up for up to minus 40 degrees, while drawing only about 10 Watts of power. Fun fact – I looked up how much -40 Fahrenheit is in Celsius, and it’s… -40 Celsius, lol. Easy to remember. In comparison a Cisco 9300 series switch will not boot up, at all. The router will also boot up in environments up to 140 degrees Fahrenheit / 60 degrees Celsius, so you could put them in the Las Vegas desert to run a solar power plant. Also elevation is a problem for normal network devices, because they often don’t work above 3000 Feet / 915 Meters.
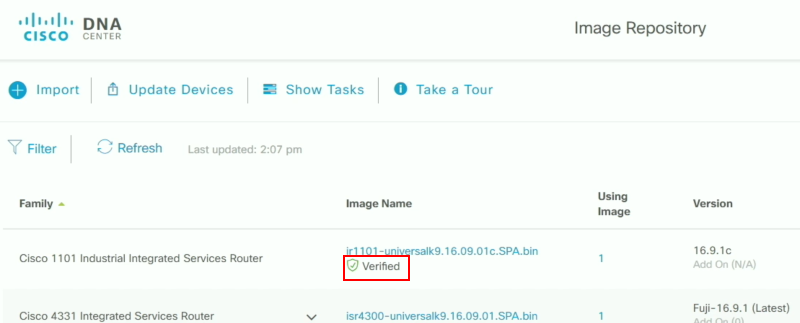
One of the biggest problems for IoT devices is that they often don’t exist in a secure environment, but they are placed in public locations, or at least in locations where unauthorized physical access is easier than in a protected data center. To enhance device security the Cisco rugged devices can be managed from Cisco DNA center, leveraging digital certificates and signed IOS images to make sure that devices cannot be easily tampered with:
Final words
It makes total sense to expand the product line to cover special deployment scenarios where normal equipment doesn’t work, or where additional functionality and security is required. To be able to include these devices into the normal IT workflow is a big bonus, because it helps avoiding having multiple non-homogeneous environments. Which also should make automation easier, and reduces training and documentation efforts.
Also, if you ever have the chance to see Tim present I can only recommend attending 🙂
Disclosure
This post is a part of my Tech Field Day post series. I was invited to this event by Gestalt IT. Gestalt IT covered travel, accommodation and food during the event duration. I did not receive any compensation for participation in this event, and I am also not obliged to blog or produce any kind of content.
Any tweets, blog articles or any other form of content I may produce are the exclusive product of my interest in technology and my will to share information with my industry peers. I will commit to share only my own point of view and analysis of the products and technologies I will be seeing/listening about during this event.



Discussions — No responses yet